https://github.com/byt3bl33d3r/DeathStar
Automating the Empire with the Death Star: getting Domain Admin with a push of a button
// underActive Directory
Ever sinceEmpireandBloodHound, pentesting Active Directory has become pretty straight forward for 95% of the environments I get dropped in.
I find myself doing the same things over and over again, and when that happens it's time to automate! After all a 'fire and forget' script that automatically gets Domain Admin has always been the dream right?
Luckily for me a lot of other awesome people (see the Shout Outs section below) did all the hard stuff already. Additionally,Empireintroduced a RESTful API a while ago making the creation of third-party scripts that interact with it a breeze.
Before I continue, I'll take this opportunity for a rant: getting Domain Admin shouldNOTbe the sole scope of your pentest and if it is you are doing it wrong. You should be focusing on post-exploitation, trying to find sensitive PII, documents etc.. anything that can clearly demonstrate to 'management' how much it could have impacted the organization if it were a real world compromise. However, having Domain Admin access does make life easier, provides additional value to the client and tends to make an impression on the Blue Team.
Project goals and implementation
Originally, I wanted something that could just takeBloodHoundsoutput, parse it, feed it toEmpireand make it follow the 'chain'. However,BloodHounddoes not take into account (at least to my knowledge) paths that could be achieved using domain privilege escalations such asGPP Passwords in SYSVOL(I personally find that one an almost every engagement).
So I wanted a more 'active' version of BloodHound with 'worm like' behavior. Additionally,Empirehas most of the core functionality ofBloodHoundcovered between all of it's modules and anything that BloodHound does functionality wise that Empire currently does not have a module for could be fairly easily implemented with one (e.g. theACL attack path update, which is insanely awesome by the way)
I decided to just stick with Empire and automate everything using it's RESTful API. This would also give me the freedom to parse a module's output as I see fit and have more control over the overall logic and user feedback.
What's it doing under the hood?
The following flow graph details pretty well (I think) what DeathStar does better than I could ever explain in a blog post.
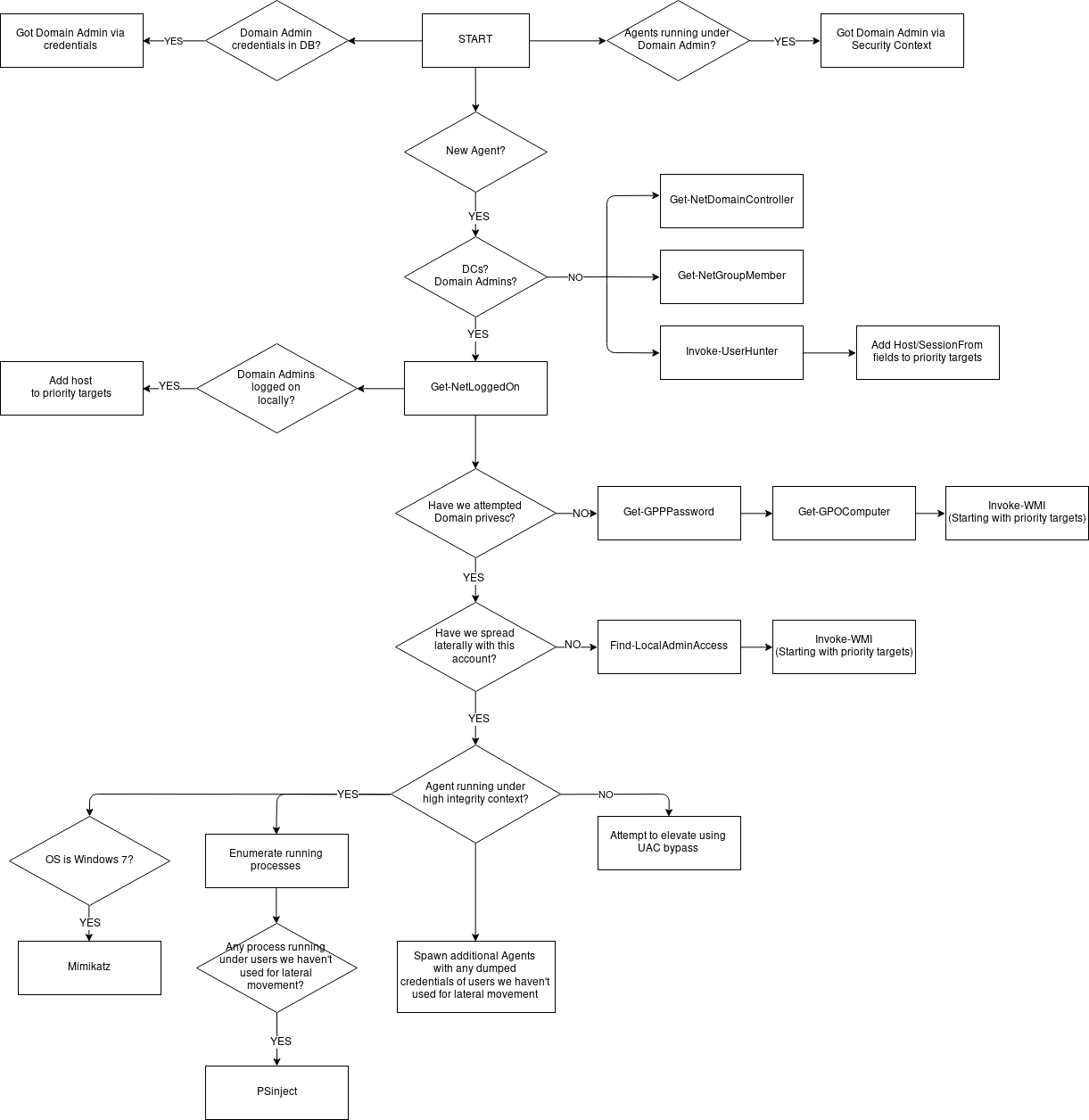
If you've pentested Active Directory recently, you should be familiar with pretty much everything in that graph. If not, feel free to hit me up and I'll be glad to answer any questions.
Setting Up
Currently, for Death Star to work you're going to have to install my fork of Empire until thispull requestgets merged and the changes get pushed to master. The fork contains some API and back-end database fixes for scripts that interact with the RESTful API.
Edit 08/28/2017 - Empire 2.1 was released, changes were merged so you can now use the main Empire repo with DeathStar :)
- DeathStar - https://github.com/byt3bl33d3r/DeathStar
- Empire - https://github.com/EmpireProject/Empire
Clone Empire, install it, then run the following:
python empire --rest --username username --password password
That will start Empire's console and RESTful API server.
To get DeathStar up and running:
git clone https://github.com/byt3bl33d3r/DeathStar
# Death Star is written in Python 3
pip3 install -r requirements.txt
# Supply the username and password you started Empire's RESTful API with
./DeathStar.py -u username -p password
If all goes well Death Star will create a http listener and you should see a 'Polling for Agents' status: this means you're authenticated to Empire's RESTful API and DeathStar is waiting for that first Agent.
All you need now is an Agent on a domain joined machine, how you do that is beyond the scope of this blog post. I'd recommend usingCrackMapExecbut I'm biased.
What does it look like in action?
Once you get that first Agent, DeathStar will take over and the magic will start.
Here are a couple of videos of DeathStar obtaining Domain Admin in two different scenarios.
In the first video, it elevates Domain privileges using theGPP Passwords in SYSVOLvulnerability, spreads laterally to the machines the GPO is applied to using the decrypted credentials and eventually lands on a machine with a Domain Admin logged in. It then enumerates running processes andPSInject'sinto a process (explorer.exe by default) running under the Domain Admin account giving us an Agent running under that security context:
<iframe width="894" height="447" src="https://www.youtube.com/embed/PTpg\_9IgxB0" frameborder="0" allow="accelerometer; autoplay; encrypted-media; gyroscope; picture-in-picture" allowfullscreen></iframe>
<iframe width="894" height="447" src="https://www.youtube.com/embed/1ZCkC8FXSzs" frameborder="0" allow="accelerometer; autoplay; encrypted-media; gyroscope; picture-in-picture" allowfullscreen></iframe>